How to Set Up a VPN Server: Beginner-to-Advanced Guide

Online privacy has become a daily concern. Public Wi-Fi networks, remote work, geo-restrictions, data tracking, and increasing surveillance have pushed many users to look for better ways to protect their internet connection. That’s where VPNs come in.
Why Do People Consider Creating Their Own VPN?
Creating a VPN is not the same as using one. Behind every secure VPN connection are encryption protocols, key management, server maintenance, and constant updates. What looks simple in theory can quickly become complex in practice - especially if privacy and security are your end goals.
While most people are familiar with commercial VPN services, a growing number of users are asking a different question: Can I create my own VPN? The idea of running a personal VPN sounds appealing: full control, no third-party providers, and the satisfaction of building something yourself. For technically curious users, it can also be a valuable learning experience.
This guide walks you through the entire journey. We’ll start with how VPNs actually work, then show you how to create your own VPN step by step. Along the way, we’ll highlight the limitations and risks of self-hosted VPNs and explain when a commercial VPN may be the more practical choice. So, you’ll have a clear answer to an important question: Is it better to build your own VPN - or use a professional solution designed to protect you from day one?
What a VPN Really Is (Before You Build One)
We’ve already touched on how VPNs work in one of our previous articles, but before diving into configuration files and server setups, it’s worth briefly revisiting the basics.
Before creating a VPN, it’s important to understand what a VPN really does. Many people associate VPNs with “complete anonymity” or “total online security,” but the reality is more nuanced.
At its core, a VPN (Virtual Private Network) creates an encrypted tunnel between your device and a VPN server. All internet traffic passing through this tunnel is protected from outside observers, such as public Wi-Fi operators, network administrators, or your internet service provider (ISP). Instead of seeing your real IP address, websites only see the IP address of the VPN server.
Behind this simple idea are three key components:
Secure Tunneling
A VPN encapsulates your internet traffic inside a secure tunnel. This prevents third parties from reading or modifying the data as it travels across the network. Even on unsecured public Wi-Fi, encrypted VPN traffic remains unreadable to attackers.
Encryption
VPNs encrypt your data before it leaves your device. Modern VPNs use strong encryption standards that make intercepted traffic practically impossible to decode without the correct keys. The strength of a VPN depends heavily on how encryption keys are generated, stored, and rotated - something that becomes especially important in self-hosted setups.
Authentication
Authentication ensures that only authorized users and devices can connect to the VPN server. This typically involves certificates, keys, or credentials that verify identity before any encrypted traffic is exchanged.
What a VPN Does Not Do
Understanding limitations is critical before building your own VPN:
- A VPN does not make you anonymous, your VPN server can still see traffic.
- A VPN does not protect you from malware, phishing, or unsafe downloads.
- A VPN does not stop websites from tracking you via cookies, logins, or browser fingerprinting.
- A self-hosted VPN does not provide shared anonymity - all traffic is tied to a single server and IP.
This distinction matters because many DIY VPNs are built with unrealistic expectations. While a personal VPN can encrypt traffic and secure connections, it does not automatically provide the same level of privacy, redundancy, or global reach as a commercial VPN infrastructure.
With these fundamentals refreshed, we can now look at when creating your own VPN actually makes sense and when it doesn’t.
When Does It Make Sense to Create Your Own VPN?
Creating your own VPN can be useful, but only in specific situations. Despite the appeal of full control and independence, a self-hosted VPN is not a universal solution for online privacy.
In practice, building your own VPN makes sense mainly for limited, well-defined use cases.
First, a DIY VPN is a good option if your goal is securing your connection on public or untrusted networks. Encrypting traffic on hotel, airport, or café Wi-Fi is one of the most practical and reliable benefits of a personal VPN.
Second, it can be useful for remote access to a private network. Many people set up VPNs to securely connect to home servers, office systems, or internal tools while traveling.
Third, creating a VPN can be valuable as a learning exercise. For users interested in networking, system administration, or cybersecurity, setting up a VPN helps build hands-on experience with encryption, authentication, and server management.
However, there are also clear limitations.
A self-hosted VPN is usually not ideal for anonymity, large-scale privacy, or bypassing geo-restrictions. Because all traffic goes through a single server with a single IP address, your activity remains linkable. There’s no shared traffic pool, no global infrastructure, and no built-in redundancy.
In short, creating your own VPN makes sense when you want control, security for a specific network, or technical experience - not when you want instant privacy, global access, or a hands-off solution.
What You Need to Create a VPN
Once you understand when creating your own VPN makes sense, the next step is knowing what’s actually required. While the idea may sound simple, a working VPN still relies on several core components.
- You’ll need a server. This can be a cloud-based virtual private server (VPS) from a hosting provider or a physical machine at home or in an office. For most beginners, a VPS is the more reliable option due to stable uptime and a public IP address.
- You’ll need an operating system. Most DIY VPN setups run on Linux because it’s lightweight, secure, and well-documented. Windows-based servers are also possible, but they typically involve more overhead and fewer community-supported tools.
- You’ll need a VPN protocol and software. This is the software layer that creates encrypted tunnels, manages authentication, and routes traffic. The specific protocol you choose will affect speed, security, and complexity - a topic we’ll cover in the next section.
- Skill and time investment. Even a basic VPN setup requires comfort with command-line tools, configuration files, and ongoing maintenance. Creating a VPN is not a one-time task - it’s an ongoing responsibility.
In short, building your own VPN doesn’t require enterprise-grade hardware, but it does require technical awareness, time, and a willingness to manage your own security stack.
Choosing the Right VPN Protocol
A VPN protocol determines how your device connects to the VPN server, how data is encrypted, and how stable and fast that connection will be. When building your own VPN, the protocol you choose directly affects both usability and security.
Common VPN Protocols Compared
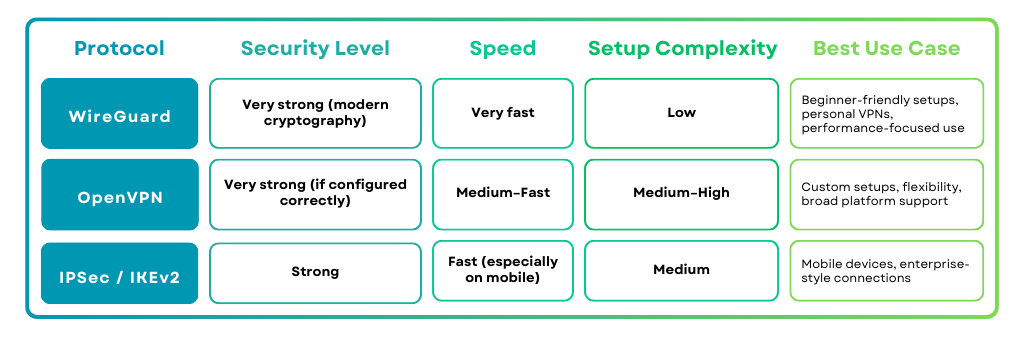
Which Protocol Should You Choose?
For most people creating a VPN for the first time, WireGuard is the easiest and most practical starting point. OpenVPN remains a solid choice for advanced customization, while IPSec is better suited to specific enterprise-style use cases.
It’s also worth noting that commercial VPN services usually support multiple protocols and automatically select the best option - something you’ll need to manage manually in a DIY setup.
With the protocol decision out of the way, we can now move on to the practical part: setting up your VPN step by step.
Step-by-Step: How to Create a VPN (Beginner Path)
Now that you’ve chosen a VPN protocol, it’s time to look at the actual setup process. While the exact commands and configurations vary depending on the protocol and server provider, the overall workflow is surprisingly consistent.
Step 1: Get a Server
Start by choosing a cloud VPS provider and creating a virtual server. Most beginners select a Linux-based server (or Raspberry Pi) because it’s lightweight, widely supported, and well-documented. Make sure the server has:
- A public IP address
- Stable uptime
- Sufficient bandwidth for your needs
Step 2: Install VPN Software
Next, install your chosen VPN software on the server. This software handles encryption, authentication, and traffic routing. Many providers offer installation scripts that simplify this step, especially for WireGuard and OpenVPN.
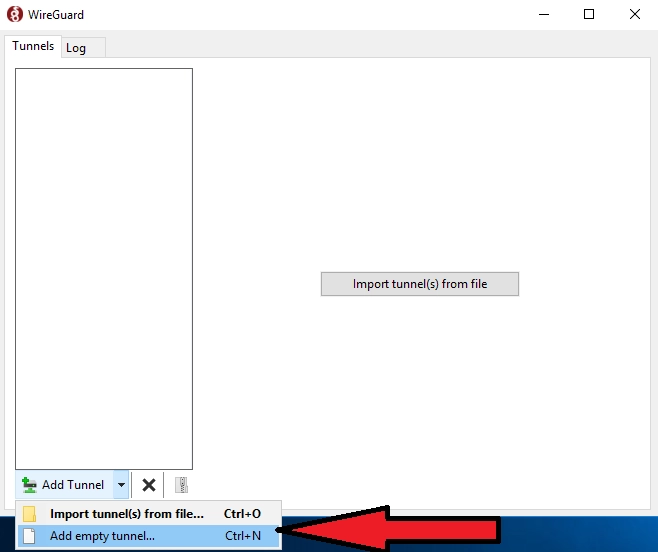
Running and adding an empty tunnel. Source: Introserv
Step 3: Generate Keys or Certificates
VPNs rely on cryptographic keys to authenticate devices. During this step, you’ll generate server and client keys or certificates. These credentials ensure that only authorized devices can connect to your VPN.
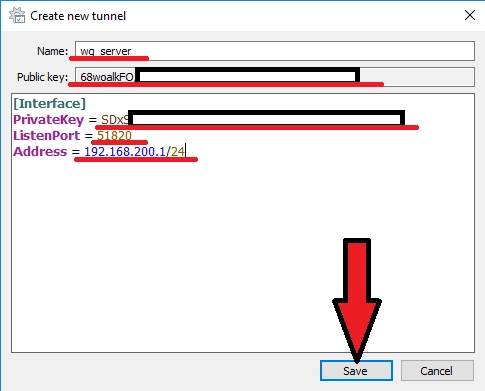
[Interface]
PrivateKey = # private key of WireGuard server
ListenPort = # port that WireGuard will listen to
Address = # desired IP address of WireGuard server
Here you need to enter the name of the network connection and public key of the WireGuard server (needed to configure the client side).
Step 4: Configure the VPN Server (Example)
This step defines how traffic flows through your VPN and what your connected devices are allowed to access. Even in a basic setup, a few core parameters must be configured.
Below is an example of what this configuration might look like using WireGuard as a reference. The same concepts apply to other protocols, even if the syntax differs.
Allowed IP Ranges
This setting defines which IP addresses a client is allowed to use through the VPN.
AllowedIPs = 10.0.0.2/32
In this example:
- The client is assigned a single internal VPN IP
- Traffic outside this range is not accepted from the client
For full internet tunneling, this value is often expanded:
AllowedIPs = 0.0.0.0/0, ::/0
This routes all traffic through the VPN tunnel.
DNS Configuration
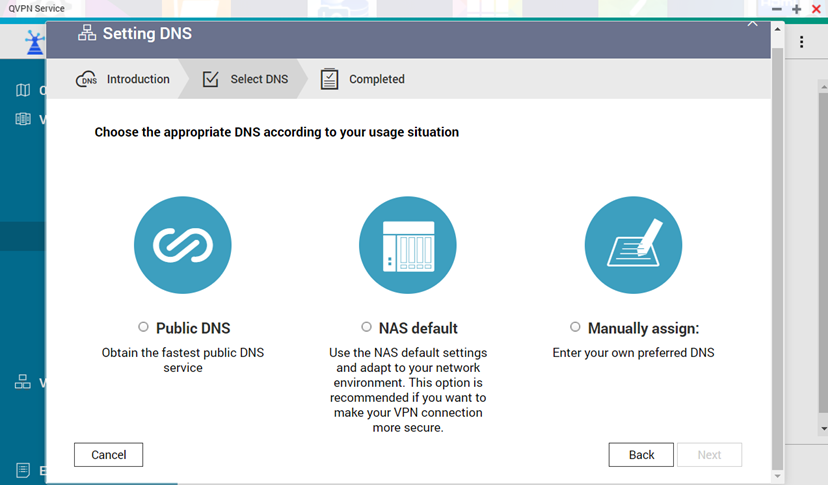
DNS Quick Wizard interface. Source: qnap
You can download the DNS Quick Wizard, which can help to choose the DNS service that best meets your needs. DNS settings determine which servers resolve domain names while connected to the VPN.
DNS = 10.0.0.1
This forces the client to use the VPN server’s DNS resolver, helping prevent DNS leaks. Without this, DNS queries may still go through the user’s ISP.
Routing Rules
Routing rules tell the system where traffic should go once it enters the VPN.
A basic setup routes traffic from the VPN interface to the public network, allowing connected devices to access the internet securely.
In practice, this means:
- VPN traffic is forwarded
- NAT (network address translation) is enabled
- Return traffic is properly routed back to the client
These steps are usually handled via system-level networking settings rather than the VPN config file alone.
Listening Ports
The listening port defines where the VPN server accepts incoming connections.
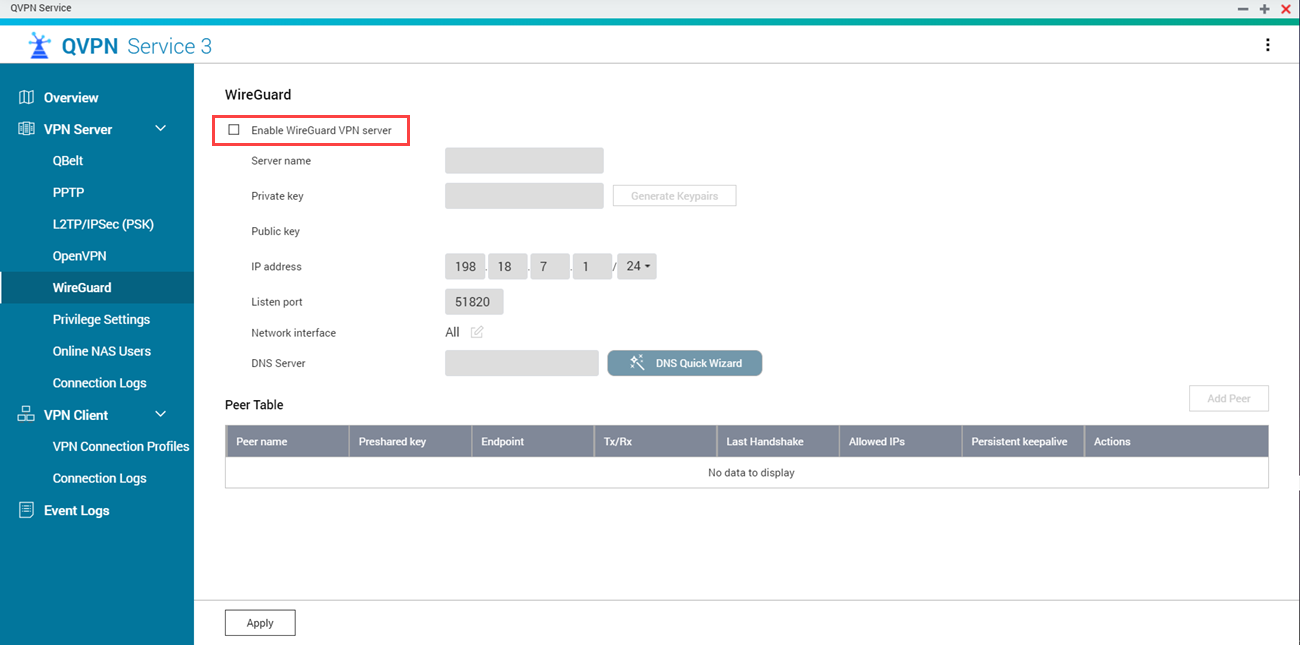
Source: qnap
Specify a UDP port number between 1 and 65535, for example:
ListenPort = 51820
This port must:
- Be open in the firewall
- Match the client configuration
- Avoid conflicts with other services
Changing the port is optional, but the firewall must always reflect the chosen value.
Why Beginners Should Start Simple?
Default configurations are designed to work safely in most scenarios. Over-customizing early on increases the risk of:
- Misrouted traffic
- DNS leaks
- Accidental exposure of services
A minimal, working configuration is always better than a complex one you don’t fully understand.
Once the basics are stable, additional security and performance tuning can be layered on gradually.
Step 5: Connect Your First Device
After the server is configured, install the VPN client on your device and import the configuration file or keys. Once connected, your traffic should be encrypted and routed through your VPN server.
Step 6: Test the Connection
Finally, verify that:
- Your IP address changes
- Traffic is encrypted
- Internet access works as expected
At this stage, you’ll have a functioning VPN.
This beginner setup is enough to secure basic connections and remote access. However, a working VPN is not the same as a hardened or privacy-optimized one - and that’s where things start to get more complex.
Advanced Setup: Customizing and Hardening Your VPN
Once your VPN is up and running, the real work begins. A default configuration may be enough for basic use, but it rarely offers optimal security or privacy. This is where advanced configuration and hardening come into play.
Below are common areas where DIY VPN setups are customized with practical examples to illustrate what’s involved.
Firewall Configuration (Traffic Control)
A firewall defines what traffic is allowed to reach your VPN server and what gets blocked. Without proper firewall rules, your server may expose unnecessary services.
Example goals:
- Allow VPN traffic only
- Block unused ports
- Prevent direct access to internal services
Typical approach:
- Allow SSH only from trusted IPs
- Allow VPN protocol ports (e.g., UDP 51820 for WireGuard)
- Drop all other inbound traffic
This step alone significantly reduces the attack surface of your VPN server.
DNS Configuration & Leak Prevention
By default, a DIY VPN may still use your ISP’s DNS servers, which can leak browsing data even if traffic is encrypted.
Common configuration choices:
- Use a private DNS resolver on the VPN server
- Force all clients to use VPN-provided DNS
- Block DNS requests outside the tunnel
What can go wrong:
- DNS queries bypass the VPN tunnel
- Websites detect your real network despite VPN usage
Preventing DNS leaks requires explicit configuration, it’s not automatic.
Kill Switch Logic (Manual Implementation)
Commercial VPNs usually include a built-in kill switch. In DIY setups, this must be implemented manually.
Concept:
- If the VPN tunnel drops, block all outbound traffic
- Prevent fallback to the regular internet connection
How it’s done:
- Firewall rules that only allow traffic via the VPN interface
- Automatic blocking when the interface goes down
This is critical if you rely on the VPN for security on public networks.
Logging & Privacy Considerations
Many DIY VPNs unintentionally log more data than expected.
Common sources of logs:
- VPN software logs
- System authentication logs
- Firewall connection logs
Even basic logs can reveal:
- Connection timestamps
- Client IPs
- Session durations
Disabling or minimizing logs requires careful configuration and ongoing monitoring - and mistakes here are common.
Example: WireGuard Configuration (Simplified)
Below is a simplified WireGuard server configuration to illustrate what advanced setups start to look like:
[Interface]
PrivateKey = <server_private_key>
Address = 10.0.0.1/24
ListenPort = 51820
SaveConfig = false
[Peer]
PublicKey = <client_public_key>
AllowedIPs = 10.0.0.2/32
Even this minimal example assumes:
- Secure key storage
- Correct firewall rulesProper routing and DNS configuration
As setups grow (multiple clients, multiple devices), complexity increases quickly.
The Hidden Cost of “Advanced” Control
Each customization adds:
- More configuration files to maintain
- More potential failure points
- More responsibility for updates and security patches
This is where many DIY VPNs become fragile, working well until something changes.
Maintaining Your Own VPN: Ongoing Security & Stability
To keep it secure and reliable, your VPN requires continuous maintenance. Unlike commercial VPN services, a self-hosted VPN has no automated security team behind it - everything depends on how well and how consistently you manage it.
Regular Updates and Patch Management
VPN software, operating systems, and encryption libraries are constantly updated to fix vulnerabilities.
If your server runs outdated components:
- Known security flaws remain exploitable
- Encryption weaknesses may go unpatched
- Attackers can target unmaintained services
A secure VPN requires frequent updates - not just once during setup, but continuously.
Key and Credential Management
Authentication keys and certificates are the backbone of VPN security. Over time, keys may:
- Become exposed
- Be reused across devices
- Remain active after devices are lost or retired
Best practice involves rotating keys periodically, revoking access for unused devices, storing keys securely, never in plain text. These steps are easy to overlook, and often are.
Monitoring and Availability
A DIY VPN has a single point of failure. If the server goes down, your VPN stops working. You are responsible for:
- Monitoring uptime
- Detecting unusual traffic or login attempts
- Restarting services after crashes or updates
Without active monitoring, failures may go unnoticed until you actually need the VPN.
Security Hardening Beyond the VPN Tunnel
A VPN only protects traffic, not the server itself. Additional security responsibilities include restricting SSH access, using strong authentication, and limiting open ports.
Preventing brute-force attacks
If the server is compromised, the VPN tunnel becomes irrelevant and attackers gain direct access.
Logging, Privacy, and Data Exposure
DIY VPNs often generate logs by default. These logs may contain:
- Connection timestamps
- Internal IP addresses
- Client identifiers
Even minimal logs can create privacy risks if stored improperly or accessed by third parties. Disabling or minimizing logs requires careful configuration and ongoing verification.
The Real Cost of Maintenance
What initially looks like a “one-time setup” quickly turns into:
- Regular security reviews
- Manual updates
- Troubleshooting unexpected issues
For technically experienced users, this may be acceptable. For most people, it becomes a long-term burden.
DIY VPN vs Commercial VPN: What’s Actually Easier?
At this point, the difference between creating your own VPN and using a commercial service becomes clear. While both approaches rely on the same underlying technologies, the experience (and the outcome) is very different.
DIY VPN vs Commercial VPN: Key Differences
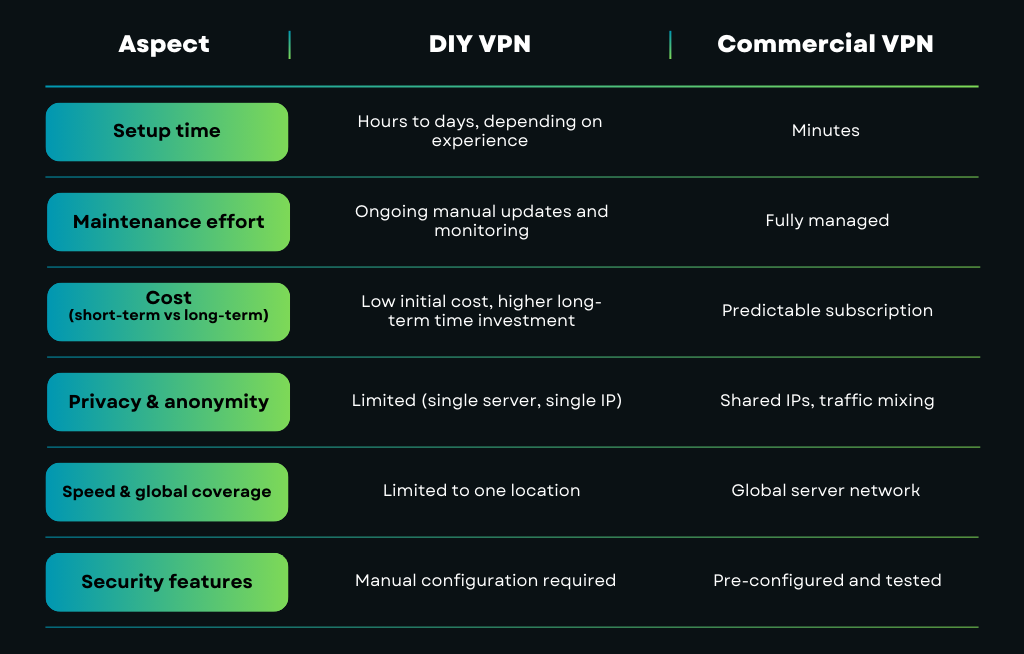
Who DIY VPNs Are Best For
A self-hosted VPN can be a reasonable choice if you:
- Want to secure a specific network or connection
- Need private remote access to home or office systems
- Enjoy hands-on server management
- Are comfortable maintaining security over time
DIY VPNs work best as tools, not as full privacy solutions.
Who Commercial VPNs Are Best For
A commercial VPN is usually the better choice if you:
- Want instant protection without technical complexity
- Care about anonymity and shared IP infrastructure
- Need access to servers in multiple countries
- Prefer automated security and regular updates
For most users, simplicity and reliability matter more than low-level control.
Why Many Users Choose a Commercial VPN Instead
Commercial VPN services are designed to solve the same problems as DIY VPNs - but without the hidden costs.
They offer:
- Pre-configured security using modern, battle-tested protocols
- Global server networks optimized for speed and stability
- No-logs policies backed by audits and transparent practices
- Instant protection across devices without manual setup
Instead of maintaining a single server, users gain access to a professionally managed infrastructure built for scale, redundancy, and privacy.
This doesn’t make DIY VPNs obsolete - but it explains why many users start with a personal VPN and later switch to a commercial solution.
In the final section, we’ll summarize when building your own VPN makes sense - and when choosing the right provider is the smarter move.
Build It Yourself, or Use the Right Tool
Building a VPN yourself can teach you a lot, but privacy isn’t measured by how complex your setup is. It’s measured by whether your data is protected, your connection is secure, and your online activity stays private - consistently and effortlessly.
If your goal is to learn, experiment, or protect a single network, a DIY VPN can be worth exploring.
If your goal is strong privacy, global access, and dependable security without setup headaches, Guru VPN delivers expert-level protection from day one.
Guru VPN is built to deliver the benefits people seek from VPNs without requiring them to become system administrators.
- High-speed servers in 49+ countries provide global access and consistent performance
- Modern protocols, including WireGuard and GuruShadow, balance speed and security automatically
- Built-in protection features, such as a Kill Switch and leak protection, work out of the box
- Easy-to-use apps make secure connections available on all major devices in seconds
- The infrastructure is maintained, updated, and monitored continuously - so users get reliable protection without technical overhead.